Human Hacking: When Fraud Gets Personal

Fraud techniques are increasingly sophisticated as technology advances. Hackers are becoming more adept at coding to exploit software vulnerabilities. However, there’s an even stronger tool in the cybercriminal’s arsenal: hacking humans. Sixty percent of data breaches are due to fraudsters abusing trust.1
As an ethical hacker, Rachel Tobac, CEO of SocialProof Security, understands fraudsters’ methods, including how they use trust against their victims. “Most successful social engineering attacks come down to a scam’s believability, not advanced technology. In a recent Synovus fraud webinar, she likened the practice to “hacking people.” “Human hacking is the art of exploiting trust. People want to be open and helpful, and that’s what attackers count on,” says Tobac.
Understanding what human hacking is and how it works is critical for organizations that want to protect both their data and their staff from evolving cyber threats.
What is hacking?
Hacking refers to the unauthorized access or manipulation of computer systems, networks or digital devices, typically with malicious intent. Cybercriminals use hacking techniques to breach security defenses, steal sensitive information, disrupt business operations or gain financial advantage.
When hacking humans, fraudsters trick individuals into engaging in risky behavior. This method was responsible for 17% of external cyberattacks in 2025 (22% in 2024).2
What do hackers do during social engineering attacks?
Hackers research employees and organizational structures to identify targets with access to financial accounts or confidential data. They then pose as trusted colleagues, vendors or authority figures to build rapport and use psychological tactics to persuade victims to reveal passwords or verification codes, click compromised links, download malicious files, grant remote computer access — even send money. Social engineering attack types vary, including fake invoices and urgent emails or phone calls from fraudsters posing as IT support.
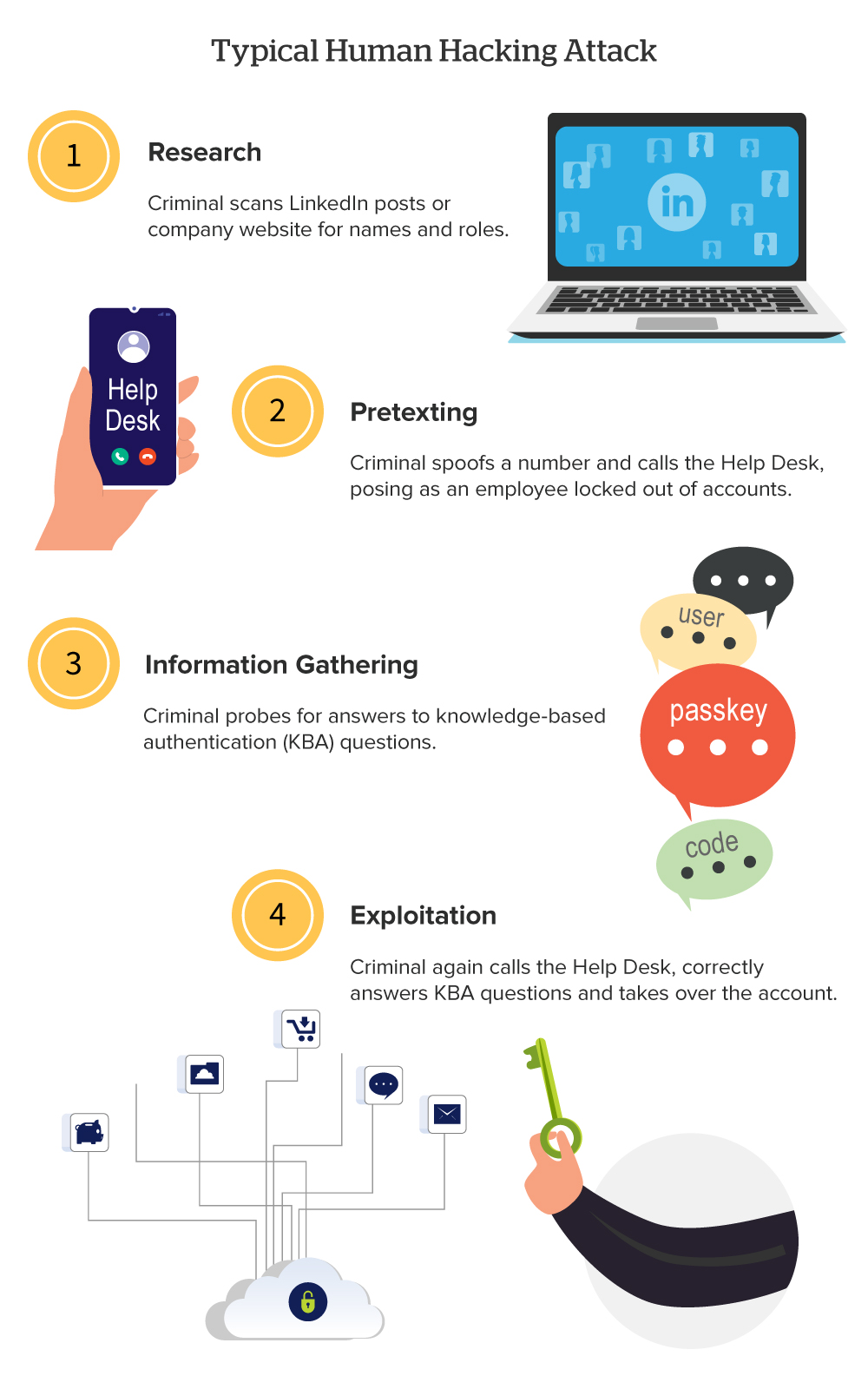
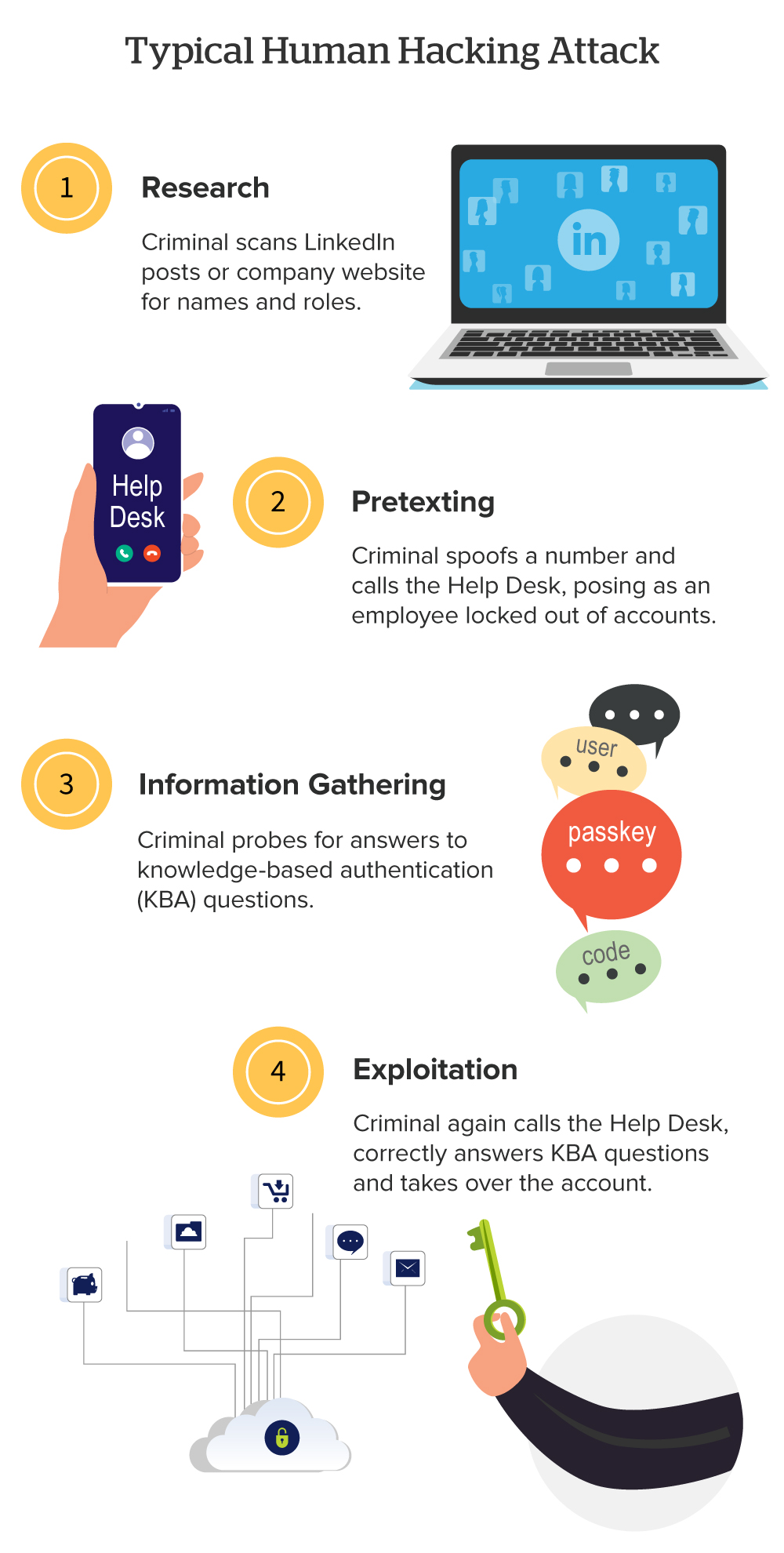
Hackers’ deceptive actions often pave the way for further exploitation, including lateral movement within the network, escalation of privileges or deployment of ransomware. The goal is to bypass technical security measures and capitalize on trust and human error, making social engineering one of the most effective — and dangerous — forms of cyberattacks against corporations.
Human hacking targets corporations with phone and text scams.
Business email compromise (BEC) attacks are less effective thanks to recent advances like strong security and multifactor authentication. In addition, Google and Yahoo’s mandatory protocols and new bulk-sender rules require one-click unsubscribe and strict spam-complaint thresholds, thereby filtering out many spoofed or unauthenticated messages before they reach the inbox.
So, fraudsters are now turning to communication channels that lack the same safeguards as email: phone calls and text messages.
Thirty percent of organizations said they suffered vishing (voice phishing) attacks in 2025.3 “Groups like Scattered Spider find LinkedIn posts that include staff roles and manager names, then target the corporation’s help desk by phone,” says Tobac.
Text and messaging scams increased about 50% compared with last year and nearly one-third of all scams now start in text or messaging apps.4
Generative AI (Gen AI) is enabling more sophisticated forms of fraud against corporations.
Scammers using Gen AI can rapidly produce highly realistic fake content, such as emails, documents, or even audio and video, that convincingly mimics trusted individuals or brands. According to Tobac, this technology enables fraudsters to scale their attacks, create more believable scams and target organizations with customized social engineering schemes that are harder for traditional security tools to detect.
Many impersonation fraud scams use Gen AI. For example, deepfakes feature video or voices that imitate company executives to trick employees into authorizing fraudulent transactions or disclosing sensitive information. In early 2025 deepfake fraud surged 1,740%.5 Forty-three percent of CIOs responding to a Gartner survey reported at least one deepfake audio call and 37% experienced deepfake video calls.6
Hackers impersonate people you know and familiar tools.
Fraudsters pose as trusted colleagues, vendors or authority figures as psychological triggers to create a sense of legitimacy and urgency. This approach to hacking humans prompts potential victims to act quickly without verifying the request. Impersonation is an effective tool for attackers seeking access to financial accounts, confidential data and valuable resources and may include various social engineering attack types.
- Technical support
Criminals pose as Microsoft or antivirus vendors seeking to install fraudulent updates to gain remote access. They may contact employees via phone calls, email, or pop-up messages to pressure individuals into granting system access or providing sensitive information, which often results in compromised networks and data loss.
- Vendor or supplier
In this scheme, fraudsters pose as legitimate business partners, vendors or suppliers to trick employees into divulging sensitive information or transferring funds. Attackers often use convincing emails, texts or phone calls that request urgent action. To defend against vendor impersonation, organizations should implement strict verification procedures and educate staff on recognizing suspicious communications.
- Coworkers
Fraudsters engaging in coworker scams often replicate the tone of genuine workplace communications, urging employees to process payments or share sensitive information before they have a chance to verify the request's authenticity. They may use internal chat or email tools.
- Banking staff
Bad actors pretend to be a financial institution’s fraud prevention staff alerting targets of fraudulent activity and asking to transfer funds to a different, “safe” account. These banking impersonation scams often use urgent messages and official-sounding language to convince victims that immediate action is necessary, making it vital to verify any requests before transferring money.
- Online jobs
Online job fraud occurs when scammers post fake employment opportunities to deceive applicants into sharing personal information, making payments or performing tasks for no legitimate compensation. These employment scams often target job seekers through convincing websites, emails or social media platforms.
- Negative reviews
Individuals or competitors post fake, damaging reviews to harm a company’s reputation and influence consumer decisions. Fraudsters use these reviews to manipulate search rankings and undermine the credibility of targeted businesses.
- Brand misrepresentation
In this scam, criminals impersonate a company's identity or products to deceive customers, damage organizational reputations or gain unauthorized financial benefits. This type of fraud can undermine consumer trust, impact search engine rankings and cause significant losses for corporations.
Corporations should be acutely aware of impersonation schemes in which fraudsters can swiftly inflict harm – sometimes without immediate detection. As more businesses rely on digital communication and remote work, the potential for human hacking schemes such as impersonation scams, fake job postings, and brand misrepresentation grows. In an interconnected workplace, a single successful scam can not only compromise company assets but also undermine consumer trust and long-term business relationships.
Hacking humans is also a gateway to ransomware attacks.
Ransomware increased 37% in 2025 and was present in almost half (44%) of all data breaches.7 This method is particularly effective because, like other hacking schemes, it requires only a temporary lapse in judgement.
Once fraudsters trick employees into granting access to a corporation’s network, they can quickly deploy ransomware that encrypts data and denies employee access until the company pays a ransom for its release. Sometimes fraudsters don’t release the data even after they receive payment or they share it with other criminals anyway.
Training employees to recognize and appropriately respond to suspicious requests is essential for reducing the risk of ransomware attacks.
Reduce your organization’s human hacking risk.
A strong security posture is the first line of defense to reduce fraud risk and protect organizational assets. An integrated and layered technology stack, which combines key components like identity verification and authentication, real-time monitoring, behavioral and data analytics, works best.
Corporations can take additional measures to mitigate human hacking schemes. Consider implementing best practices to further protect your organization from fraudsters hacking humans.
- Limit details shared on social media or public sites.
Implement clear guidelines for what employees can share on social media, as attackers often gather information from these platforms to create targeted attacks. For example, don’t share project details, vendor names or other proprietary information on public pages. Use team addresses (e.g., accounting@company.com) instead of direct email addresses and remove unnecessary job titles.
- Use internal identification methods to verify employees.
To verify employees’ identities, use internal data. Instead of birthdates or phone extensions, check against private employee numbers or other organization-issued credentials.
- Verify requests for payment before completing transactions.
Exercise extreme caution and delay responses to “urgent” requests for payment. Confirm the legitimacy of such requests through a well-established, trusted, secondary communication channel. Never rely solely on emails or texts. Instead, develop a protocol for managing payment requests that includes approval responsibility and contact information early on.
- Conduct periodic phishing simulations.
Phishing simulations expose employees to realistic examples of social engineering attempts in a safe environment. These exercises help staff recognize the tactics attackers use, such as deceptive emails or urgent requests, and practice responding appropriately without risking actual data or assets.
When responding to requests for information, Tobac recommends a “politely paranoid” approach. “Take a moment to verify requesters are actually who they say they are before clicking, sharing or sending details,” she says.
Don’t wait to protect your organization from social engineering attacks.
Empower your team with the knowledge and tools they need to identify and stop human hacking now. For more information on how our experienced banking and fraud professionals can help, complete a short form and a Synovus Treasury & Payment Solutions Consultant will contact you with more details. You can also stop by one of our local branches.
Fraud and Risk Management
Will Your Organization Make the Fraud 'Naughty or Nice' List?
Fraud and Risk Management
How Quick Service Restaurants Can Prevent Fraud and Protect Profits in 2025
Fraud and Risk Management
Guide to Cybersecurity Insurance: Why Your Organization Needs It
-
Expert Financial Strategies for Public Schools and Colleges Facing Rising Costs and Enrollment Declines
Is your institution facing declining enrollment? These financial strategies for public schools and colleges will help address rising costs and intense competition for students.
-
Interest Rates News: First Quarter 2026
See the most recent FOMC rate developments for Q1 2026, including key forecasts and practical borrowing strategies. Explore how adjustments in interest rates can affect your loans, mortgage options and overall business expansion plans.
Important disclosure information
This content is general in nature and does not constitute legal, tax, accounting, financial or investment advice. You are encouraged to consult with competent legal, tax, accounting, financial or investment professionals based on your specific circumstances. We do not make any warranties as to accuracy or completeness of this information, do not endorse any third-party companies, products, or services described here, and take no liability for your use of this information.
- DeepStrike, “Phishing Statistics 2025: AI-Driven Attacks, Costs & Trends,” April 29, 2025 Back
- Verizon, “2025 Data Breach Investigations Report,” May 2025 Back
- DeepStrike, “Phishing Statistics 2025: AI-Driven Attacks, Costs & Trends,” April 29, 2025 Back
- Consumer Reports, “Texting and Messaging Scam Attempts Increased by 50 Percent,” October 1, 2025 Back
- Global Cyber Alliance, “Seeing Isn’t Believing: Stay Safe During the Deepfake Revolution,” May 28, 2025 Back
- Gartner, “Why CIOs Can’t Ignore the Rising Tide of Deepfake Attacks,” September 2, 2025 Back
- Verizon, “2025 Data Breach Investigations Report,” May 2025 Back
